GTmetrix experienced a 10% increase in job runtime after patching for Meltdown and Spectre
Two new critical vulnerabilities have been revealed affecting all hardware using Intel, AMD and ARM based processors. The Meltdown and Spectre hardware bugs allow attackers to access privileged data in memory. Both likely affect all modern processors – including the ones your servers use to host your website.
What are Meltdown and Spectre exactly and how do they work?
Generally speaking, Meltdown and Spectre are exploits that can be used to extract restricted data (like passwords, e-mails, photos, etc.) from memory used by other applications.

Meltdown is a bug that “melts” the security limitations placed by the hardware between the operating system and applications, allowing it to access restricted data in memory.

Spectre is a bug that essentially tricks applications into sharing data, thereby potentially revealing secrets and restricted information.
Who do they affect?
Basically everybody. This includes laptops, desktops, servers, tablets, mobile devices – anything with a modern processor.
More specifically, only Intel processors are verified to be affected by Meltdown (so far), however – Intel, AMD and ARM processors are all confirmed to be affected by Spectre.
If you are working with sensitive-information on an unpatched processor and/or OS, there is a risk of that information being leaked. This is especially the case with shared hosting, as well as cloud-based, virtualized hosting (eg. Amazon EC2), where many users share the same physical machine.
How do they affect GTmetrix?
On December 28th, 2017, our test servers were patched to protect against Meltdown and Spectre vulnerabilities. Upon reboot, we noticed an increase in job runtime – roughly a 10% increase to the norm.
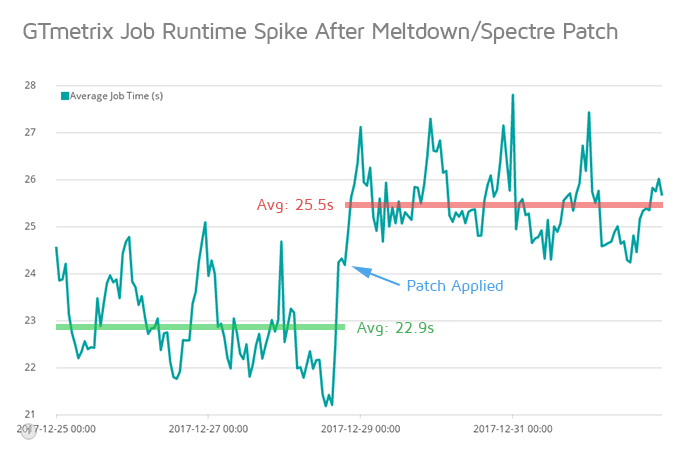
After tracking the results of hundreds of thousands of website tests per day, the trend was sustained, consistent and translated to roughly 2 seconds of additional runtime for GTmetrix tests. The bulk of this time is most likely due to extra overhead required for hardening the the user-to-kernel and kernel-to-user transitions to mitigate Meltdown and Spectre.
In terms of how this will affect your page load performance, this will depend on how your backend code stresses your hardware – there could be a minimal increase in backend/waiting time for all your resources, or up to 20% higher (Source).
This means your site may load slower than usual – but here are some things to note:
- This does not mean a 10% increase in your Fully loaded time
There’s only a possibility of an increase in server/Backend time and waiting time (page generation, TTFB, etc). All other aspects of your website are unaffected, including PageSpeed and YSlow scores. - Resource intensive sites are more affected
Complex sites that are dynamic and require a lot of resources to generate content will likely be more impacted by these patches.
What can you do?
Unfortunately, there’s not much you can do about this at the moment. The vulnerabilities are new, and it will take some time for the majority of web servers on the Internet to be patched.
System administrators running servers will need to patch them when the patches are eventually released. A few larger services are already patched:
However, these patches are all on the Host side. The OS on the VMs themselves also need to be patched, but as far as we can tell, there aren’t any OSes with updated kernels yet.
At the moment, all we can do is wait for these patches, and hope that their impact on server performance is negligible.
Learn more about the Meltdown/Spectre exploits, including technical papers and reports here: Meltdown and Spectre